0. IaC

1. AWS CloudFormation(Azure Resource Manager, GCP Deployment Manager)
1.1 Resource 파일 생성
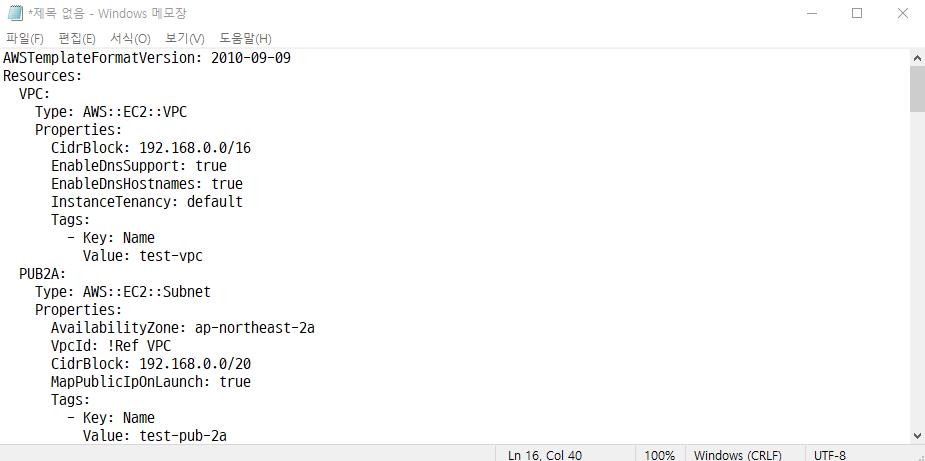
# vi test-vpc.yaml
AWSTemplateFormatVersion: 2010-09-09
Resources:
VPC: ## 논리적 이름; 내가 정할 수 있다.
Type: AWS::EC2::VPC
Properties:
CidrBlock: 192.168.0.0/16
EnableDnsSupport: true
EnableDnsHostnames: true
InstanceTenancy: default
Tags:
- Key: Name
Value: test-vpc
PUB2A:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2a
VpcId: !Ref VPC
CidrBlock: 192.168.0.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-2a
PUB2B:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2b
VpcId: !Ref VPC
CidrBlock: 192.168.16.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-2b
PUB2C:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2c
VpcId: !Ref VPC
CidrBlock: 192.168.32.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-2c
PUB2D:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2d
VpcId: !Ref VPC
CidrBlock: 192.168.48.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-2d
PVT2A:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2a
VpcId: !Ref VPC
CidrBlock: 192.168.64.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-2a
PVT2B:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2b
VpcId: !Ref VPC
CidrBlock: 192.168.80.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-2b
PVT2C:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2c
VpcId: !Ref VPC
CidrBlock: 192.168.96.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-2c
PVT2D:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2d
VpcId: !Ref VPC
CidrBlock: 192.168.112.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-2d
InternetGateway:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: test-igw
VPCGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
InternetGatewayId: !Ref InternetGateway
PUBRTB:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: test-pub-rtb
PVTRTB:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: test-pvt-rtb
InternetRoute:
Type: AWS::EC2::Route
DependsOn: InternetGateway
Properties:
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
RouteTableId: !Ref PUBRTB
PUB2ARTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2A
PUB2BRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2B
PUB2CRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2C
PUB2DRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2D
PVT2ARTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2A
PVT2BRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2B
PVT2CRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2C
PVT2DRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2D
# vi test-ec2.yaml
AWSTemplateFormatVersion: 2010-09-09
Mappings:
RegionMap:
ap-northeast-2:
AMIID: ami-03db74b70e1da9c56
ap-northeast-1:
AMIID: ami-0df2ca8a354185e1e
Parameters:
InstanceType:
Type: String
Default: t2.micro
Description: Enter instance size. Default is t2.micro
VPC:
Type: String
Default: vpc-01a276b266db7833b
Description: VPC ID.
Subnet:
Type: String
Default: subnet-01132b9dddcf71d3d
Description: Subnet ID.
AMI:
Type: String
Default: AMIID
Description: The Linux AMI to use.
Key:
Type: String
Default: test-key
Description: The key used to access the instance.
Resources:
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupName: "test-sg-web"
GroupDescription: "test-sg-web"
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: '80'
ToPort: '80'
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: '22'
ToPort: '22'
CidrIp: 123.142.252.25/32
- IpProtocol: icmp
FromPort: '-1'
ToPort: '-1'
CidrIp: 0.0.0.0/0
SecurityGroupEgress:
- IpProtocol: -1
CidrIp: 0.0.0.0/0
EC2Insteance:
Type: AWS::EC2::Instance
Properties:
SubnetId: !Ref Subnet
# ImageId: !Ref AMI
ImageId: !FindInMap [ RegionMap, !Ref "AWS::Region", !Ref AMI ]
InstanceType:
Ref: InstanceType
KeyName: !Ref Key
SecurityGroupIds:
- Ref: InstanceSecurityGroup
BlockDeviceMappings:
- DeviceName: /dev/xvda
Ebs:
VolumeSize: 8
- DeviceName: /dev/xvdb
Ebs:
VolumeSize: 8
Tags:
- Key: Name
Value: test-ec2
UserData:
Fn::Base64: |
#cloud-boothook
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello World!" > /var/www/html/index.html
Outputs:
PublicIp:
Description: PublicIp Output
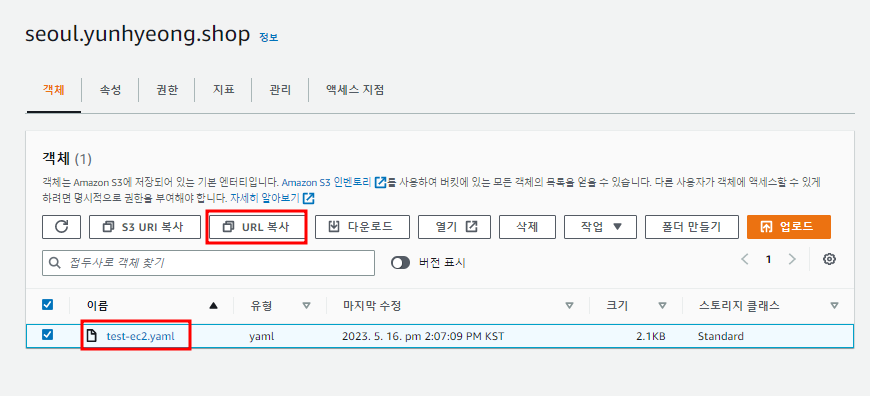
Value: {"Fn::GetAtt": ["EC2Insteance","PublicIp"]}- 위의 내용을 복사
- yaml 파일 만들기
- 복사한 내용을 붙여 넣는다.
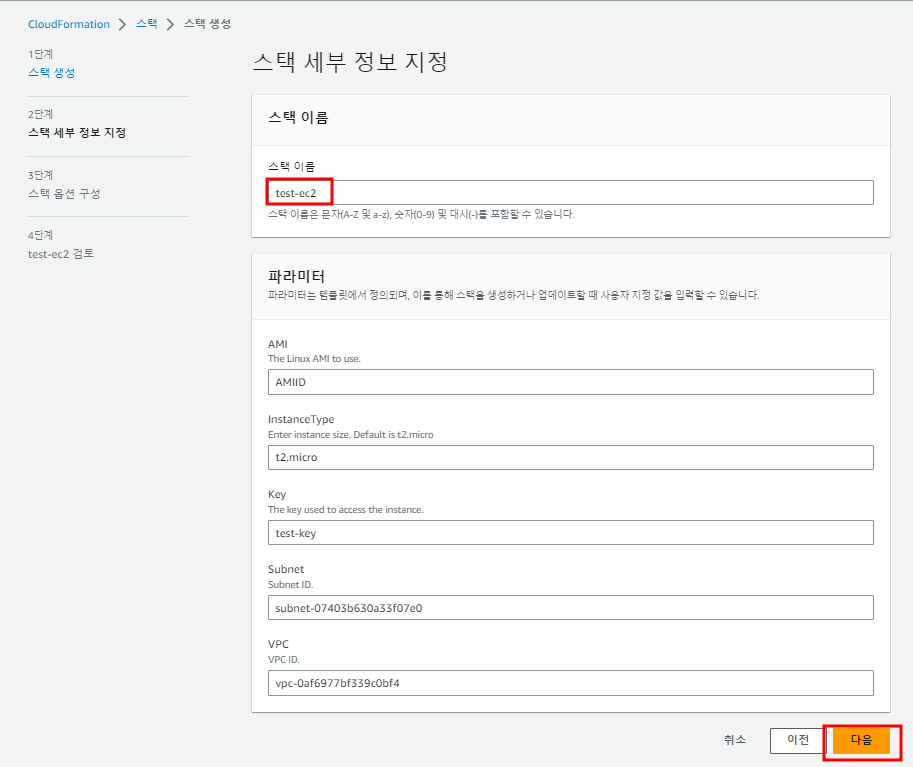
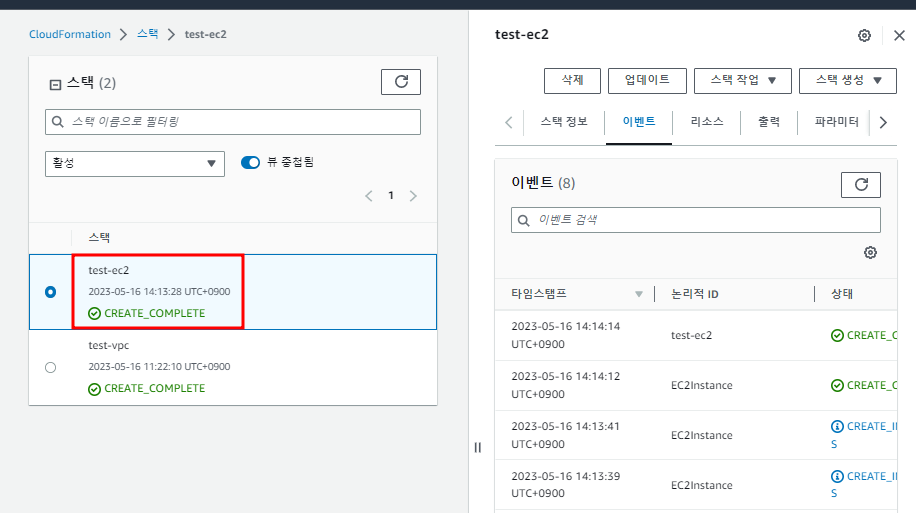
1.2 CloudFormation 스택 생성


- CloudFormation은 자체적으로 저장 공간이 없기 때문에 파일을 업로드 하면 S3에 자동으로 공간이 만들어진다.

- 스택 옵션 구성은 생략
- 이대로 스택을 생성한다.
1.3 Mappings, Parameters, Resources, Ec2 instance
AWSTemplateFormatVersion: 2010-09-09
Mappings:
RegionMap:
ap-northeast-2:
AMIID: ami-035da6a0773842f64
ap-northeast-1:
AMIID: ami-08928044842b396f0
Parameters:
InstanceType:
Type: String
Default: t2.micro
Description: Enter instance size. Default is t2.micro
VPC:
Type: String
Default: vpc-0af6977bf339c0bf4
Description: VPC ID.
Subnet:
Type: String
Default: subnet-07403b630a33f07e0
Description: Subnet ID.
AMI:
Type: String
Default: AMIID
Description: The Linux AMI to use.
Key:
Type: String
Default: test-key
Description: The key used to access the instance.
Resources:
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupName: "test-sg-web"
GroupDescription: "test-sg-web"
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: '80'
ToPort: '80'
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: '22'
ToPort: '22'
CidrIp: 123.142.252.25/32
- IpProtocol: icmp
FromPort: '-1'
ToPort: '-1'
CidrIp: 0.0.0.0/0
SecurityGroupEgress:
- IpProtocol: -1
CidrIp: 0.0.0.0/0
EC2Instance:
Type: AWS::EC2::Instance
Properties:
SubnetId: !Ref Subnet
ImageId: !FindInMap [ RegionMap, !Ref "AWS::Region", !Ref AMI ]
InstanceType:
Ref: InstanceType
KeyName: !Ref Key
SecurityGroupIds:
- Ref: InstanceSecurityGroup
BlockDeviceMappings:
- DeviceName: /dev/xvda
Ebs:
VolumeSize: 8
- DeviceName: /dev/xvdb
Ebs:
VolumeSize: 8
Tags:
- Key: Name
Value: test-ec2
UserData:
Fn::Base64: |
#cloud-boothook
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello World!" > /var/www/html/index.html
Outputs:
PublicIp:
Description: PublicIp Output
Value: {"Fn::GetAtt": ["EC2Instance","PublicIp"]}- test-ec2.yaml 파일 만들기


2. Tokyo CloudFormation
1.1 Resource 파일 생성

- 서울 리전의 key를 tokyo-key로 변경하여 도쿄리전으로 보낸다
# vi test-vpc.yaml
AWSTemplateFormatVersion: 2010-09-09
Resources:
VPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: 192.168.0.0/16
EnableDnsSupport: true
EnableDnsHostnames: true
InstanceTenancy: default
Tags:
- Key: Name
Value: test-vpc
PUB2A:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1a
VpcId: !Ref VPC
CidrBlock: 192.168.0.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-1a
PUB2C:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1c
VpcId: !Ref VPC
CidrBlock: 192.168.32.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-1c
PUB2D:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1d
VpcId: !Ref VPC
CidrBlock: 192.168.48.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-1d
PVT2A:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1a
VpcId: !Ref VPC
CidrBlock: 192.168.64.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-1a
PVT2C:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1c
VpcId: !Ref VPC
CidrBlock: 192.168.96.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-1c
PVT2D:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1d
VpcId: !Ref VPC
CidrBlock: 192.168.112.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-1d
InternetGateway:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: test-igw
VPCGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
InternetGatewayId: !Ref InternetGateway
PUBRTB:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: test-pub-rtb
PVTRTB:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: test-pvt-rtb
InternetRoute:
Type: AWS::EC2::Route
DependsOn: InternetGateway
Properties:
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
RouteTableId: !Ref PUBRTB
PUB2ARTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2A
PUB2BRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2B
PUB2CRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2C
PUB2DRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2D
PVT2ARTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2A
PVT2BRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2B
PVT2CRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2C
PVT2DRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2D
AWSTemplateFormatVersion: 2010-09-09
Resources:
VPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: 192.168.0.0/16
EnableDnsSupport: true
EnableDnsHostnames: true
InstanceTenancy: default
Tags:
- Key: Name
Value: test-vpc
PUB1A:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1a
VpcId: !Ref VPC
CidrBlock: 192.168.0.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-1a
PUB1C:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1c
VpcId: !Ref VPC
CidrBlock: 192.168.32.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-1c
PUB1D:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1d
VpcId: !Ref VPC
CidrBlock: 192.168.48.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-1d
PVT1A:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1a
VpcId: !Ref VPC
CidrBlock: 192.168.64.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-1a
PVT1C:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1c
VpcId: !Ref VPC
CidrBlock: 192.168.96.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-1c
PVT1D:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1d
VpcId: !Ref VPC
CidrBlock: 192.168.112.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-1d
InternetGateway:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: test-igw
VPCGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
InternetGatewayId: !Ref InternetGateway
PUBRTB:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: test-pub-rtb
PVTRTB:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: test-pvt-rtb
InternetRoute:
Type: AWS::EC2::Route
DependsOn: InternetGateway
Properties:
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
RouteTableId: !Ref PUBRTB
PUB1ARTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB1A
PUB1CRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB1C
PUB1DRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB1D
PVT1ARTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT1A
PVT1CRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT1C
PVT1DRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT1D
- test-vpc-tokyo.yaml 파일을 만들고 S3에 업로드
# vi test-ec2-tokyo.yaml
AWSTemplateFormatVersion: 2010-09-09
Mappings:
RegionMap:
ap-northeast-1:
AMIID: ami-08928044842b396f0
ap-northeast-2:
AMIID: ami-035da6a0773842f64
Parameters:
InstanceType:
Type: String
Default: t2.micro
Description: Enter instance size. Default is t2.micro
VPC:
Type: String
Default: vpc-0217a9890f3e74e8e
Description: VPC ID.
Subnet:
Type: String
Default: subnet-07ba1bcb85733fa10
Description: Subnet ID.
AMI:
Type: String
Default: AMIID
Description: The Linux AMI to use.
Key:
Type: String
Default: tokyo-key
Description: The key used to access the instance.
Resources:
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupName: "test-sg-web"
GroupDescription: "test-sg-web"
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: '80'
ToPort: '80'
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: '22'
ToPort: '22'
CidrIp: 106.253.56.124/32
- IpProtocol: icmp
FromPort: '-1'
ToPort: '-1'
CidrIp: 0.0.0.0/0
SecurityGroupEgress:
- IpProtocol: -1
CidrIp: 0.0.0.0/0
EC2Insteance:
Type: AWS::EC2::Instance
Properties:
SubnetId: !Ref Subnet
ImageId: !FindInMap [ RegionMap, !Ref "AWS::Region", !Ref AMI ]
InstanceType:
Ref: InstanceType
KeyName: !Ref Key
SecurityGroupIds:
- Ref: InstanceSecurityGroup
BlockDeviceMappings:
- DeviceName: /dev/xvda
Ebs:
VolumeSize: 8
- DeviceName: /dev/xvdb
Ebs:
VolumeSize: 8
Tags:
- Key: Name
Value: test-ec2
UserData:
Fn::Base64: |
#cloud-boothook
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello Tokyo!" > /var/www/html/index.html
Outputs:
PublicIp:
Description: PublicIp Output
Value: {"Fn::GetAtt": ["EC2Insteance","PublicIp"]}
- test-ec2-tokyo.yaml 파일을 만들고 S3에 업로드
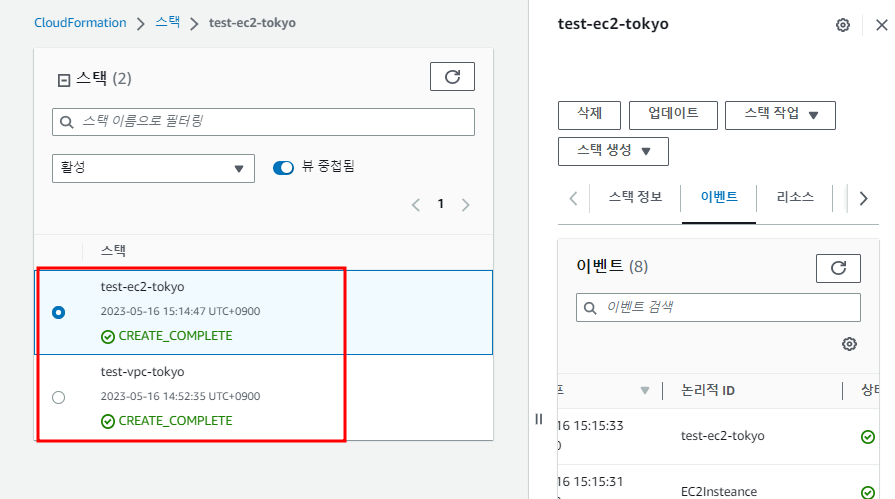
- CloudFormation에서 vpc와 ec2 s3 주소를 복사하여 스택 생성
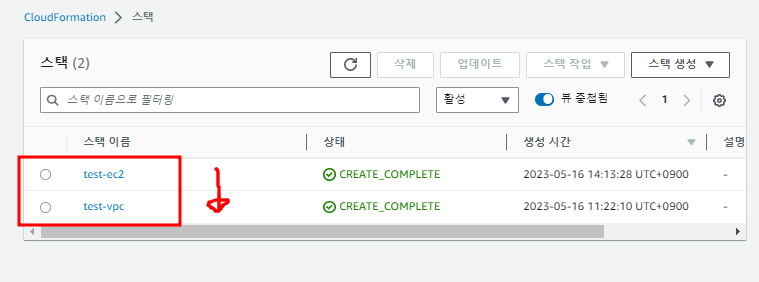
3. 삭제하기
- ec2 -> vpc 순서대로 삭제
- 키페어는 키페어 항목에서 직접 삭제
4. Terraform
--- Terraform 이란?
과거 시스템 관리자는 인프라를 수동으로 구축하고 관리했습니다. 그리고 모든 서버, 데이터베이스, 로드 밸런서, 네트워크를 수작업으로 생성하고 관리했기 때문에 서버 다운, 구성 실수, 배포 오류가 자주 발생하였습니다. 테라폼은 간단한 선언적 언어를 사용하여 인프라를 코드로 정의합니다. 몇 가지 명령을 사용하여 AWS, Azure, GCP 같은 다양한 퍼블릭 클라우드 공급자와 오픈스택, ESXi 같은 프라이빗 클라우드와 가상화 플랫폼에서 해당 인프라를 배포 및 관리하게 합니다.
--- Terraform 작동 방식
테라폼은 해시코프사에서 Go언어로 개발한 오픈소스도구입니다. 운영체제마다 바이너리 파일이 존재하는데 Go 코드는 하나의 바이너리 파일로 컴파일되며 Terraform이라는 명령어로 실행할 수 있습니다. 이 Terraform 명령어를 사용하여 노트북, 데스크탑, 빌드 서버 또는 다른 컴퓨터에서든 인프라를 배포할 수 있으며 이를 위해 추가 인프라(마스터, 에이전트)를 생성할 필요가 없습니다. 즉 Terraform 명령어가 AWS, Azure, GCP, Openstack 등의 Provider를 대신해 API를 호출하여 리소스를 생성합니다.
테라폼은 생성하려는 인프라 정보가 담겨 있는 텍스트로 이루어진 테라폼 구성 파일을 생성하여 API를 호출합니다. 이러한 구성 값들이 '코드형 인프라'를 만드는 바로 그 '코드'입니다. 팀의 누군가가 인프라를 수정하고자 할 때, 서버에 직접 접속하여 작업하거나 수작업으로 수정하는 대신 테라폼을 사용하여 구성 파일을 수정할 있습니다.
--- Terraform 주요 명령어
- *.tf 스크립트 작성
- terraform init : terraform 명령어에는 테라폼의 기본 기능이 포함되어 있지만 모든 공급자(AWS, Azure, GCP 등)에 대한 코드가 포함되어 있지 않습니다. 그렇게 때문에 terraform init 명령어를 실행하여 테라폼에 코드를 스캔하도록 지시하고 어느 공급자인지 확인하고, 필요한 코드를 다운로드하도록 해야 합니다. 기본적으로 공급자 코드는 테라폼의 .terraform 폴더에 플러그인 형태로 다운로드됩니다.
- terraform plan : 테라폼이 구성 파일을 사용하여 작업을 수행하기 전에 코드의 온전성을 검사할 수 있습니다. plan 명령어는 리눅스에서 쓰이는 diff 명령의 결괏값과 유사합니다. + 가 있는 항목은 추가되고, - 가 있는 항목은 삭제된다는 뜻입니다. ~ 가 있는 항목은 수정됩니다.
- terraform apply : 테라폼의 구성 파일을 실행하려면 terraform apply 명령어를 실행합니다.

- 사용자 키 확인
yum install -y yum-utils
yum-config-manager --add-repo https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo
yum -y install terraform
ls -al
cat credentials
export AWS_ACCESS_KEY_ID=AKIAYNJP452DQTRR2O4U
export AWS_SECRET_ACCESS_KEY=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- Terraform 설치
- aws cli 자격증명때 사용한 키를 넣어준다.
# mkdir terraform
# mkdir tf-test && cd $_
# vi main.tf
provider "aws" {
region = "ap-northeast-2"
}
resource "aws_instance" "example" {
ami = "ami-035da6a0773842f64"
instance_type = "t2.micro"
vpc_security_group_ids = [aws_security_group.instance.id]
user_data = <<-EOF
#!/bin/bash
#cloud-boothook ## 사용자 데이터 변경시 변경 내용을 적용하는 명령어
yum install -y httpd
systemctl enable --now httpd
echo "<h1>example</h1>" > /var/www/html/index.html
EOF
tags = {
Name = "terraform-example"
}
}
resource "aws_security_group" "instance" {
name = var.security_group_name
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "tf-web"
}
}
variable "security_group_name" {
description = "The name of the security group"
type = string
default = "terraform-example-instance"
}
output "public_ip" {
value = aws_instance.example.public_ip
description = "The public IP of the Instance"
}
# terraform init
# terraform plan
# terraform apply
# terraform destroy- ec2 생성
- 변경 사항 생기면 terraform plan 후 terraform apply
'Cloud Solution Architect > AWS' 카테고리의 다른 글
| Amazon - EKS (0) | 2023.06.12 |
|---|---|
| Terraform - VPC, EC2, Autoscaling (0) | 2023.05.18 |
| AWS-CLI (0) | 2023.05.15 |
| 2차 세미 프로젝트 - Openstack (0) | 2023.05.11 |
| AWS - Amazon Inspector, CloudWatchLog, NAT Instance (0) | 2023.05.02 |